The Silent Risk in Every Image: Why You Must Remove EXIF Data Before Sharing
In today’s digital-first world, every small piece of information matters — sometimes more than we realize.
You might think sending an innocent photo of your office, team, or even a product prototype is harmless.

But hidden inside almost every image you take is a set of invisible information called EXIF data — and it could be silently leaking your personal or business details. Let’s dive into what EXIF data is, why it can be dangerous, and how you can easily remove it before sharing images.
What is EXIF Data?
EXIF (Exchangeable Image File Format) is a bundle of metadata automatically embedded into images when they are captured by a digital camera, smartphone, or editing software.
This metadata can include:
- GPS coordinates (latitude, longitude, altitude)
- Device details (phone model, camera type)
- Date and time the photo was taken
- Camera settings like shutter speed, ISO, focal length
- Editing history and software used
In short: every photo carries a fingerprint that reveals a lot more than just the image itself.

How You May Be Sharing EXIF Data Unknowingly
You might be exposing sensitive EXIF information without even realizing it when you:
- Email images directly as attachments.
- Send original images over WhatsApp, Slack, or other messaging platforms (especially if not compressed).
- Upload raw photos to websites, blogs, or client portals.
- Share screenshots — some Mac/Windows tools preserve metadata even in screenshots.
Most apps or platforms don’t automatically strip EXIF data — meaning whatever is attached stays attached unless you actively remove it.
The Real Risks of Exposing EXIF Data
When you unknowingly share EXIF data, you expose yourself (and your organization) to various risks:
🛰 Revealing Sensitive Locations
An office photo could include GPS coordinates pointing directly to your company’s location, your team member’s homes, or confidential project sites.
🕵️♂️ Leaking Insider Information
Device names, editing history, or folder paths embedded in EXIF can reveal internal project names, tools you use, or development stages — valuable for competitors or malicious actors.
🛡 Breaching Client Confidentiality
If you are in a service-based business, sending client-related photos without scrubbing metadata could breach NDAs or confidentiality agreements.
In short, EXIF data is a hidden treasure map for cybercriminals, social engineers, and corporate spies.
How to Remove EXIF Data (The Right Way)
Thankfully, removing EXIF data isn’t complicated. Here’s how you can do it safely depending on your system:
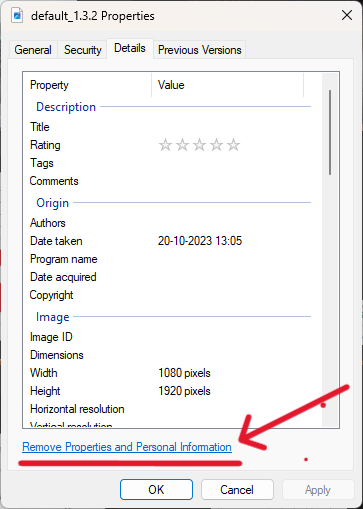
1. On Windows:
- Right-click the image file → choose Properties.
- Go to the Details tab.
- Click Remove Properties and Personal Information at the bottom.
- Choose Create a copy with all possible properties removed or manually select which data to erase.
Quick and easy!
2. On Mac:
Mac Preview allows you to view EXIF data (Tools → Show Inspector → Info Tab → GPS), but unfortunately, it does not remove metadata natively.

- Download ImageOptim — a free, safe tool.
- Drag and drop your images into ImageOptim.
- It will automatically strip out unnecessary metadata without affecting image quality.
Taking a fresh screenshot of an image often removes most metadata, but this might compress or reduce quality — so use it carefully.
3. On Android
Google Photos: When you share a photo via Google Photos, it automatically strips location data (unless you manually allow it).
Manual Removal Apps: Use free apps like Photo Metadata Remover or Scrambled Exif. These apps allow you to easily remove metadata before sharing images.
4. On iPhone
Share Without Metadata:
When you tap the Share button on a photo ➔ Tap Options at the top ➔ Turn off Location and All Photo Data before sending.
Manual Removal Apps:
Apps like Metapho (free with paid options) or ViewExif let you view and remove metadata directly from your iPhone.
Use Online Tools (if needed)
If you don’t want to install anything, there are reputable online tools that can help you:
Upload your image → review or remove metadata → download the cleaned version.
(Note: Don’t use online tools for highly confidential images — always better to handle them locally.)
General Best Practices to Stay Safe
- 🔒 Always compress images before uploading or sending — many compression tools remove metadata automatically.
- 🔒 Use a photo editor like Photoshop, GIMP, or Paint.NET to export images without metadata.
- 🔒 When using social media, check platform settings — some platforms (like Facebook) strip metadata on upload, but many others don’t.
- 🔒 Educate your team and employees — make “metadata hygiene” a regular part of your security policies.
Final Thoughts
Small data leaks often cause big problems. Protecting your EXIF data is a simple but powerful step toward securing your digital presence – both personally and professionally.
At Nurture IT, we believe that true security isn’t just about firewalls and antivirus — it’s about awareness, hygiene, and smart habits across the organization.
Need help creating a customized security checklist for your team?
Or looking for safer cloud collaboration solutions that protect your metadata automatically?
Reach out to us — let’s make your digital life safer, smarter, and stress-free.
About Nurture IT
Nurture IT, one of the leading IT service providers in Bangalore offers customized scalable technology solutions specifically designed for our client’s unique needs.
As a preferred partner to technology leaders like Lenovo, Dell, Apple, HP, Asus, Tata, Google, Microsoft, Cisco, Sophos, Jamf, Soti, Fortinet, Poly, Octa, Seclore, Seqrite we deploy the most advanced business technology solutions to ensure optimal reliability, productivity, and value.
Our B2B branch, Nurture IT, adeptly serves corporate and scaling-up demands. Conversely, for those not anticipating immediate growth, our Retail division – Laptop World caters to your specific needs. Make an informed choice aligned with your organizational trajectory and immediate necessities.