If you are using Fortinet SSL-VPN devices, it’s time to take action
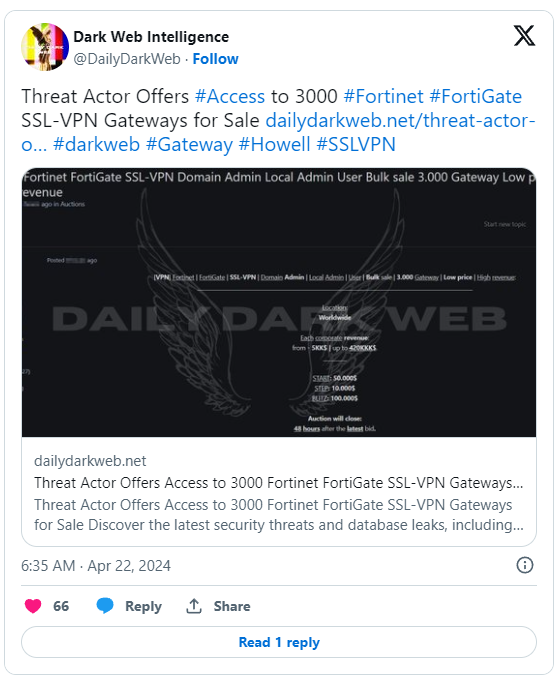
In recent cybersecurity news, a tweet from DailyDarkWeb has sent shockwaves through the industry, highlighting the exploitation of vulnerabilities in Fortinet SSL-VPN devices. Today’s FlashUpdate serves as a crucial alert to businesses relying on Fortinet devices for secure remote access to corporate networks.

The Vulnerability found on Fortinet SSL-VPN devices
Fortinet devices have long been trusted by organizations worldwide for their robust security features. However, this breach has uncovered a critical flaw that could potentially grant unauthorized access to sensitive data and internal networks. Reports suggest that hackers are exploiting these vulnerabilities to offer administrative access to over 3000 Fortinet SSL-VPN devices, posing a grave threat to affected organizations.
Understanding the Impact
The ramifications of this breach are severe and far-reaching. From Data theft and Ransomware attacks to significant Reputational damage, the potential consequences cannot be understated. While Fortinet has yet to issue a formal response, users must remain vigilant for updates and act swiftly to mitigate risks.
Taking Action
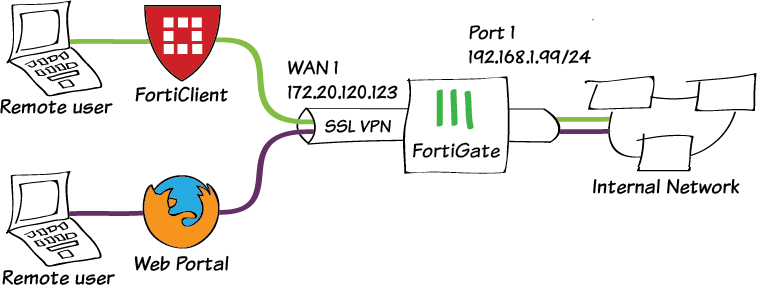
In light of these developments, here are essential steps organizations should take to safeguard their networks –
- Prompt Security Audit: Conduct an immediate assessment of all Fortinet SSL-VPN devices to identify any vulnerabilities and assess the extent of the breach.
- Update Firmware: Ensure that all devices are running the latest firmware and security patches provided by Fortinet. Timely updates are critical to addressing known vulnerabilities and strengthening defenses against potential threats.
- Enhance Monitoring: Implement robust monitoring measures to track network traffic and detect any unusual access patterns. By enhancing visibility into network activities, organizations can swiftly identify and respond to suspicious behavior.
- Employee Education: Educate employees about cybersecurity best practices and the risks associated with potential threats. Encourage them to remain vigilant and report any suspicious activities promptly.
Conclusion
The exploitation of vulnerabilities in Fortinet SSL-VPN devices serves as a stark reminder of the persistent threats lurking in the digital landscape. As businesses navigate an increasingly complex cybersecurity landscape, proactive measures are essential to safeguarding sensitive data and protecting against potential breaches. By staying informed, remaining vigilant, and implementing robust security protocols, organizations can mitigate risks and uphold the integrity of their networks in the face of evolving cyber threats.
About Nurture IT
At Nurture IT, one of the leading IT service providers in Bangalore, we’re on a mission to empower businesses with cutting-edge technology solutions tailored to their specific requirements. As you navigate the ever-evolving digital landscape, cybersecurity vigilance is paramount. That’s why we’re here to equip you with the tools and expertise needed to stay ahead of potential threats.
With our extensive range of Infosec, Cybersecurity, and End Point Security products from industry-leading brands like Fortinet, Sophos, BitDefender, Cisco, and more, we offer comprehensive protection against a myriad of cyber risks. From threat detection and prevention to data encryption and network security, our solutions are designed to fortify your defenses and safeguard your critical assets.
Don’t leave your business vulnerable to cyber attacks. Partner with Nurture IT today and take proactive steps to secure your digital infrastructure. Together, we’ll ensure your business remains resilient, protected, and poised for success in today’s digital age.
Our B2B branch, Nurture IT, adeptly serves corporate and scaling-up demands. Conversely, for those not anticipating immediate growth, our Retail division – Laptop World caters to your specific needs. Make an informed choice aligned with your organizational trajectory and immediate necessities